Brute-Forcing SHA-256 Hashes in Go: A Comprehensive Guide
Nov 10, 2024 · 8 min read · Brute Force SHA-256 Password Security Go Programming Cybersecurity Techniques Ethical Hacking Concurrency in Go Software Engineering ·
In the world of cybersecurity, brute-forcing hashes can be both an educational and practical exercise, especially for understanding password security and hash functions. In this post, we will explore a Go application that brute-forces a given SHA-256 hash by generating random passwords and checking their hash against a …
Read MoreGrover's Algorithm: Unveiling Quantum Computing's Search Superpower
Jul 4, 2024 · 3 min read · Grover's Algorithm Quantum Computing Quantum Algorithms Cryptography Quantum Supremacy Database Search Optimization ·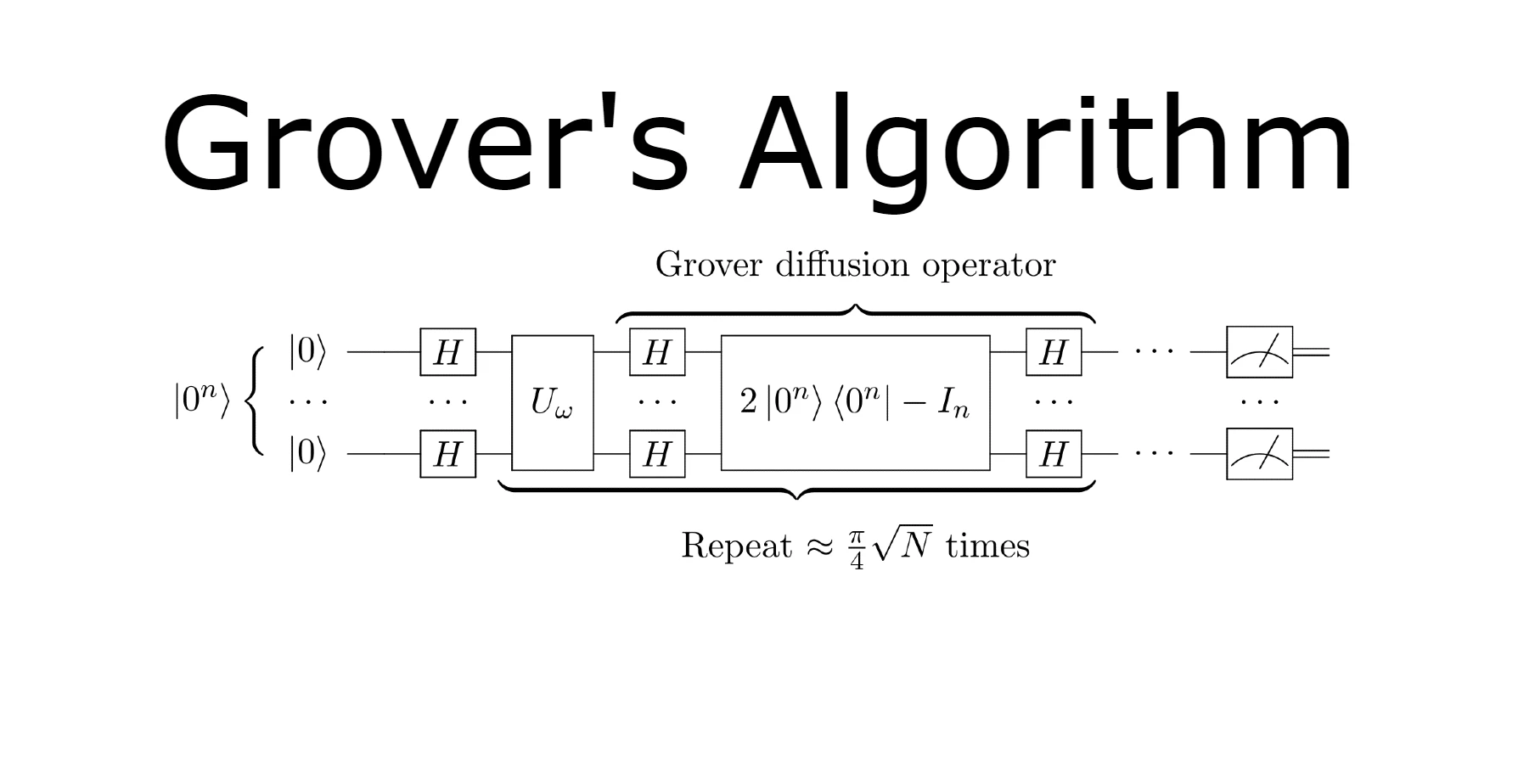
In the realm of quantum computing, where traditional rules of computation blur, Grover's algorithm stands as a shining example of quantum supremacy in specific problem domains. Named after Lov Grover, who introduced it in 1996, this algorithm promises to revolutionize search problems by providing an exponential speedup …
Read MoreCracking SHA-256 with Quantum Computers: Myth vs Reality
Jul 3, 2024 · 2 min read · SHA-256 Quantum Algorithms Grover's Algorithm Quantum Computing Cryptographic Security Cybersecurity Threats ·
In the realm of cybersecurity, SHA-256 (Secure Hash Algorithm 256-bit) stands as a formidable wall against unauthorized access and data tampering. Widely used in cryptographic applications, SHA-256 generates a unique 256-bit hash value for any given input, making it practically impossible to reverse engineer through …
Read More