I/P Transducers: Bridging Pneumatics and Electronics in Industrial Automation

In industrial automation, achieving seamless communication between electronic and pneumatic systems is critical. I/P transducers, or Current-to-Pressure transducers, serve as the bridge between these two realms. They convert an electrical input signal (commonly a 4–20 mA current) into a proportional pneumatic output, …
Read MoreExploring KS40 and KS50: Key Features and Applications of Industrial Temperature Controllers
Nov 17, 2024 · 6 min read · KS40 Controller KS50 Controller Temperature Regulation PID Control Process Optimization Industry 4.0 Smart Manufacturing HVAC Systems Industrial Electronics ·
In industrial environments where precise temperature control is critical, specialized controllers like KS40 and KS50 offer the reliability and functionality required for optimal performance. Manufactured with advanced control algorithms and customizable settings, these controllers cater to a range of industries, from …
Read MoreWater Ring Compressors: Principles, Benefits, and Industrial Applications
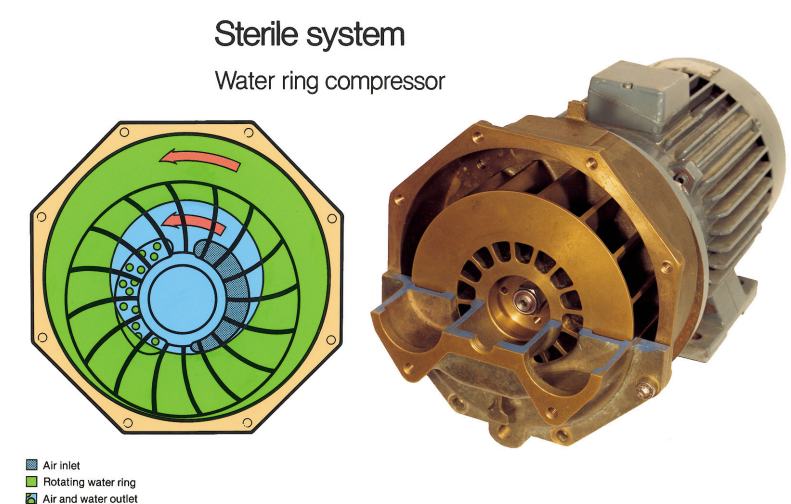
Water ring compressors, also known as liquid ring compressors, are a type of positive displacement compressor that uses water (or another compatible liquid) as a sealant. Their unique design allows them to effectively compress gases and create vacuums without generating significant heat, making them highly efficient …
Read MoreUnderstanding Constant-Pressure Modulating Valves: A Key Component for Optimizing Fluid Control Systems
In many fluid control systems, maintaining a constant pressure is essential for system stability, efficiency, and safety. Constant-pressure modulating valves (CPMVs) are designed to achieve just that—keeping pressure at a stable level despite variations in flow rate, load changes, or system conditions. CPMVs are widely …
Read MoreExploring Solid-State Flow Sensors: The Future of Accurate and Reliable Fluid Measurement

As technology advances, industries demand more precise and dependable measurement tools. Traditional mechanical flow sensors, though effective, have limitations such as wear and tear, which can impact their lifespan and accuracy. Enter solid-state flow sensors—innovative devices that eliminate moving parts, resulting …
Read MoreBrute-Forcing SHA-256 Hashes in Go: A Comprehensive Guide
Nov 10, 2024 · 8 min read · Brute Force SHA-256 Password Security Go Programming Cybersecurity Techniques Ethical Hacking Concurrency in Go Software Engineering ·
In the world of cybersecurity, brute-forcing hashes can be both an educational and practical exercise, especially for understanding password security and hash functions. In this post, we will explore a Go application that brute-forces a given SHA-256 hash by generating random passwords and checking their hash against a …
Read More