Cracking SHA-256 with Quantum Computers: Myth vs Reality

In the realm of cybersecurity, SHA-256 (Secure Hash Algorithm 256-bit) stands as a formidable wall against unauthorized access and data tampering. Widely used in cryptographic applications, SHA-256 generates a unique 256-bit hash value for any given input, making it practically impossible to reverse engineer through brute force on classical computers.
However, the rise of quantum computing has sparked speculation about the future security of SHA-256 and similar algorithms. Quantum computers, leveraging quantum mechanics to perform computations at unprecedented speeds, promise to revolutionize many fields, including cryptography.
Understanding Quantum Computing
Quantum computers operate fundamentally differently from classical computers. While classical computers use bits that represent either 0 or 1, quantum computers use qubits that can represent 0, 1, or both simultaneously (superposition). This allows quantum computers to perform computations exponentially faster for certain types of problems, including factoring large numbers and searching large databases.
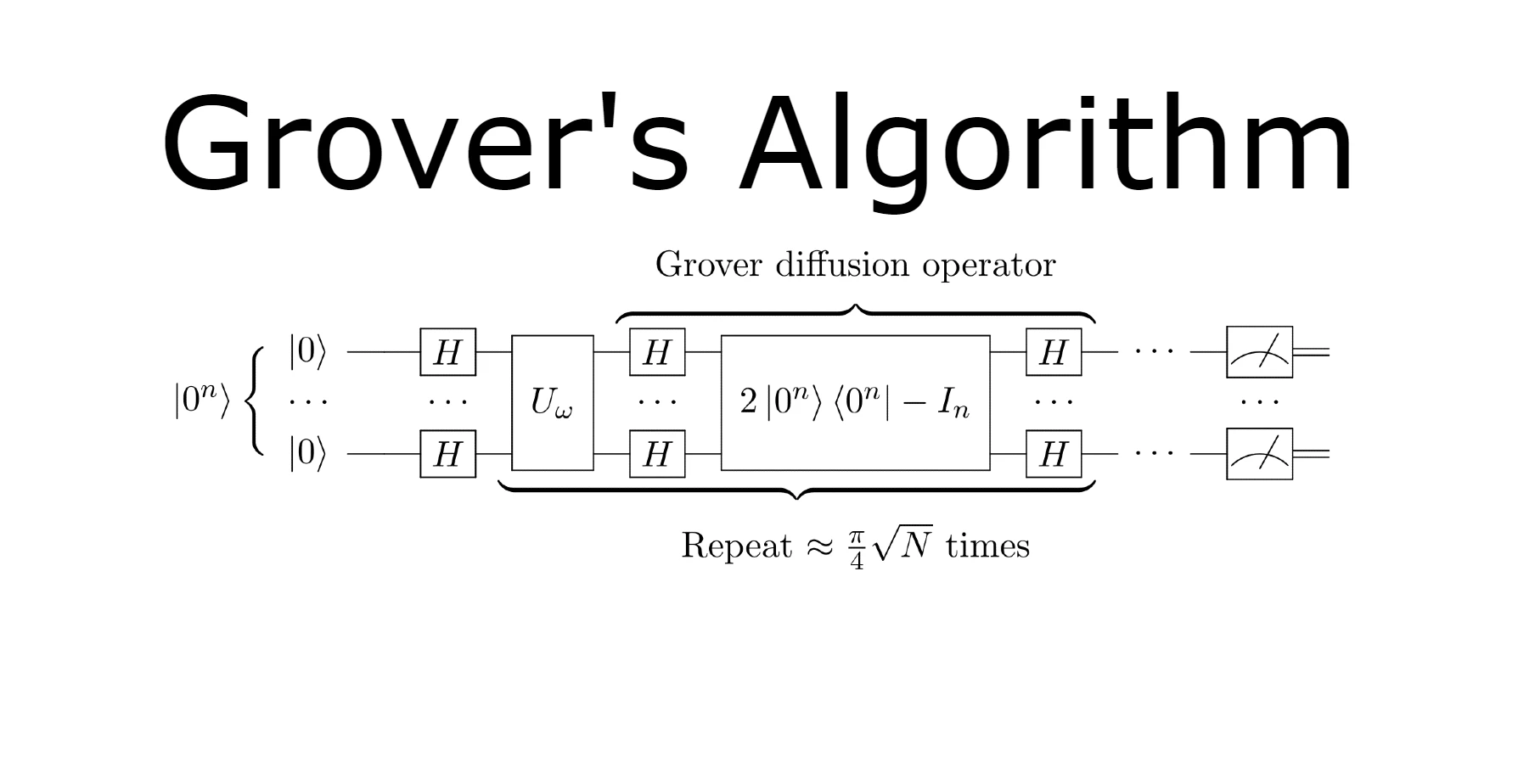
Grover's Algorithm and Quantum Attacks
One of the quantum algorithms relevant to breaking cryptographic algorithms like SHA-256 is Grover's algorithm. Grover's algorithm can search an unsorted database of N entries in roughly √N steps, whereas a classical computer would require O(N) steps. This quadratic speedup means that a quantum computer using Grover's algorithm could potentially reduce the complexity of cracking SHA-256 from 2^256 (theoretically secure against brute force attacks on classical computers) to 2^128 operations, which is still formidable but significantly less secure.
Practical Implications and Current Realities
Despite these theoretical possibilities, several practical challenges remain before quantum computers can threaten SHA-256:
- Qubit Stability: Quantum computers today are prone to errors due to decoherence, making it challenging to maintain stable qubits long enough to perform complex computations reliably.
- Scale and Infrastructure: Building large-scale quantum computers capable of executing algorithms like Grover's at scale is a significant engineering feat, requiring precise control over quantum states and cooling mechanisms.
- Cryptographic Evolution: Researchers are actively developing quantum-resistant cryptographic algorithms that can withstand attacks from quantum computers, ensuring data security in the post-quantum era.
Conclusion
While the prospect of quantum computers breaking SHA-256 is a concern for future cybersecurity, it remains a complex and distant reality. Current quantum computers are still in their infancy, and practical quantum attacks on SHA-256 are not yet feasible. The cybersecurity community continues to monitor developments in quantum computing and cryptography, preparing for a future where quantum-resistant algorithms may be necessary.
In summary, while SHA-256 remains secure against classical computing attacks, the advent of quantum computing presents both challenges and opportunities for the field of cryptography, driving innovation towards more resilient and secure cryptographic standards.