Grover's Algorithm: Unveiling Quantum Computing's Search Superpower
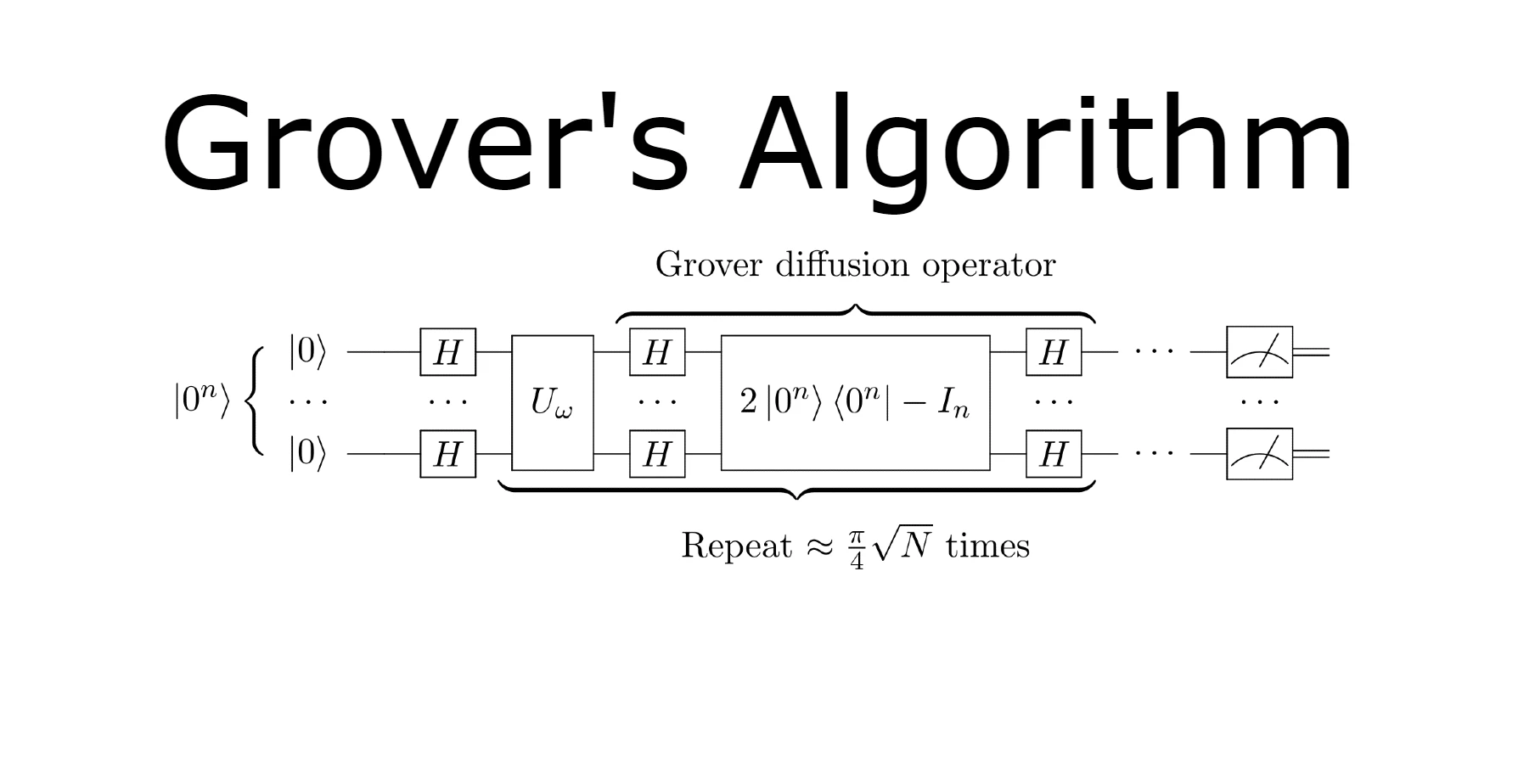
In the realm of quantum computing, where traditional rules of computation blur, Grover's algorithm stands as a shining example of quantum supremacy in specific problem domains. Named after Lov Grover, who introduced it in 1996, this algorithm promises to revolutionize search problems by providing an exponential speedup over classical algorithms.
Understanding Grover's Algorithm
At its core, Grover's algorithm addresses the problem of searching an unsorted database, a task that is classically linear in complexity. For a database with N items, a classical computer would typically require on average N/2 operations to find a specific item. In contrast, Grover's algorithm achieves this with only about √N operations, marking a quadratic speedup.
Quantum Mechanics Underpinning
The power of Grover's algorithm stems from its exploitation of quantum superposition and interference:
- Superposition: Quantum bits or qubits can exist in a state of 0, 1, or both simultaneously due to superposition. This property allows quantum computers to compute on a massive parallel scale.
- Interference: By carefully manipulating qubits through quantum gates, Grover's algorithm leverages interference to amplify the amplitude of the correct solution state while suppressing others.
How Grover's Algorithm Works
- Initialization: Start with qubits in a uniform superposition state, representing all possible states of the search space.
- Oracle Function: Introduce an oracle function that marks the solution state. In quantum computing, the oracle is implemented as a quantum operation that flips the sign of the solution state's amplitude.
- Amplification: Iteratively apply the oracle function followed by a phase inversion operation across all qubits. This amplification process boosts the probability of measuring the solution state.
- Measurement: After several iterations (approximately √N times), the algorithm probabilistically collapses to the solution state. Measurement at this point yields the desired solution with high probability.
Applications of Grover's Algorithm
Grover's algorithm's implications extend across various fields:
- Cryptography: It poses a theoretical threat to symmetric cryptographic algorithms like AES and hash functions such as SHA-256 by potentially reducing their security margins.
- Database Search: Accelerates searching through unsorted databases, which is beneficial in data retrieval and analysis.
- Optimization: Can be adapted for optimization problems, such as finding the minimum or maximum value of a function, with applications in machine learning and logistics.
Challenges and Limitations
Despite its potential, Grover's algorithm faces several challenges:
- Qubit Stability: Quantum computers require stable qubits to maintain coherence during computation, which remains a technical hurdle.
- Scalability: Scaling up quantum computers to handle larger problem sizes with more qubits and controlling them reliably is a significant engineering challenge.
- Cryptographic Adaptation: The development of quantum-resistant cryptographic algorithms is essential to mitigate potential vulnerabilities posed by quantum computing.
Future Directions
As quantum computing technology advances, researchers continue to explore enhancements and applications of Grover's algorithm:
- Algorithmic Improvements: Refining quantum circuits and operations to optimize performance and reduce error rates.
- Hardware Development: Innovations in qubit technology and error correction codes to improve quantum computer reliability and scalability.
- Cryptography: Developing and standardizing quantum-resistant cryptographic protocols to ensure data security in the quantum era.
Conclusion
Grover's algorithm stands at the forefront of quantum computing's transformative potential, showcasing its ability to outperform classical algorithms in specific problem domains. As quantum computing continues to mature, understanding the principles and capabilities of algorithms like Grover's is crucial for navigating the future landscape of computation and cryptography.


