The Evolution of Encryption: From Simple Ciphers to Advanced Algorithms
Sep 6, 2024 · 6 min read · encryption cryptography cybersecurity data protection digital security history of encryption encryption algorithms modern encryption cybersecurity evolution ·
In an age where digital data is both a priceless asset and a prime target for malicious actors, encryption has become one of the most critical tools in securing information. Encryption, the process of converting information into a code to prevent unauthorized access, has undergone a remarkable transformation over the …
Read MoreGrover's Algorithm: Unveiling Quantum Computing's Search Superpower
Jul 4, 2024 · 3 min read · Grover's Algorithm Quantum Computing Quantum Algorithms Cryptography Quantum Supremacy Database Search Optimization ·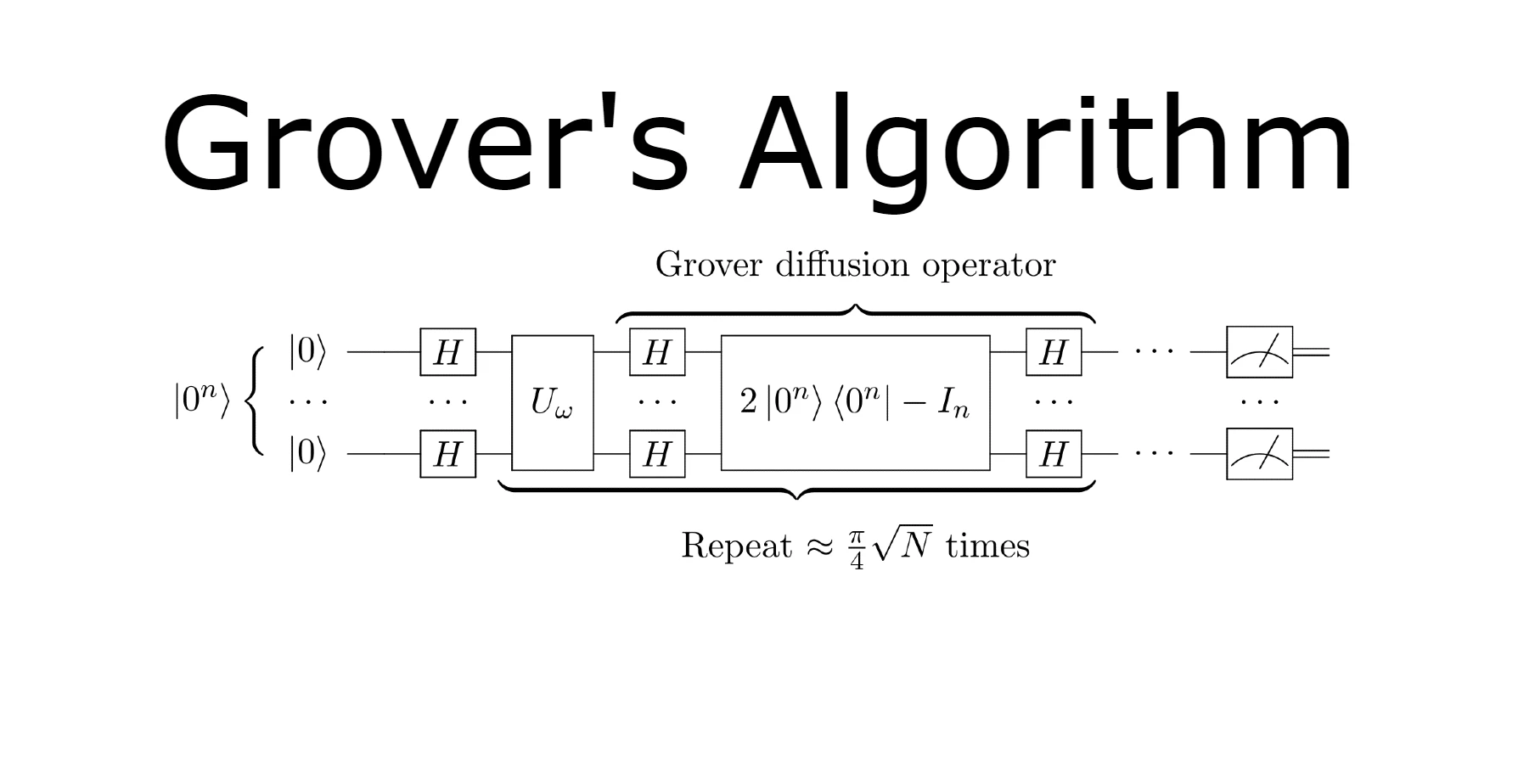
In the realm of quantum computing, where traditional rules of computation blur, Grover's algorithm stands as a shining example of quantum supremacy in specific problem domains. Named after Lov Grover, who introduced it in 1996, this algorithm promises to revolutionize search problems by providing an exponential speedup …
Read More
Hash functions, such as SHA-256, are integral to modern cryptography, ensuring data integrity and security. They are designed to be one-way functions—easy to compute but practically impossible to reverse. However, with enough computational power and persistence, brute force attacks can crack these hashes. In this blog …
Read More